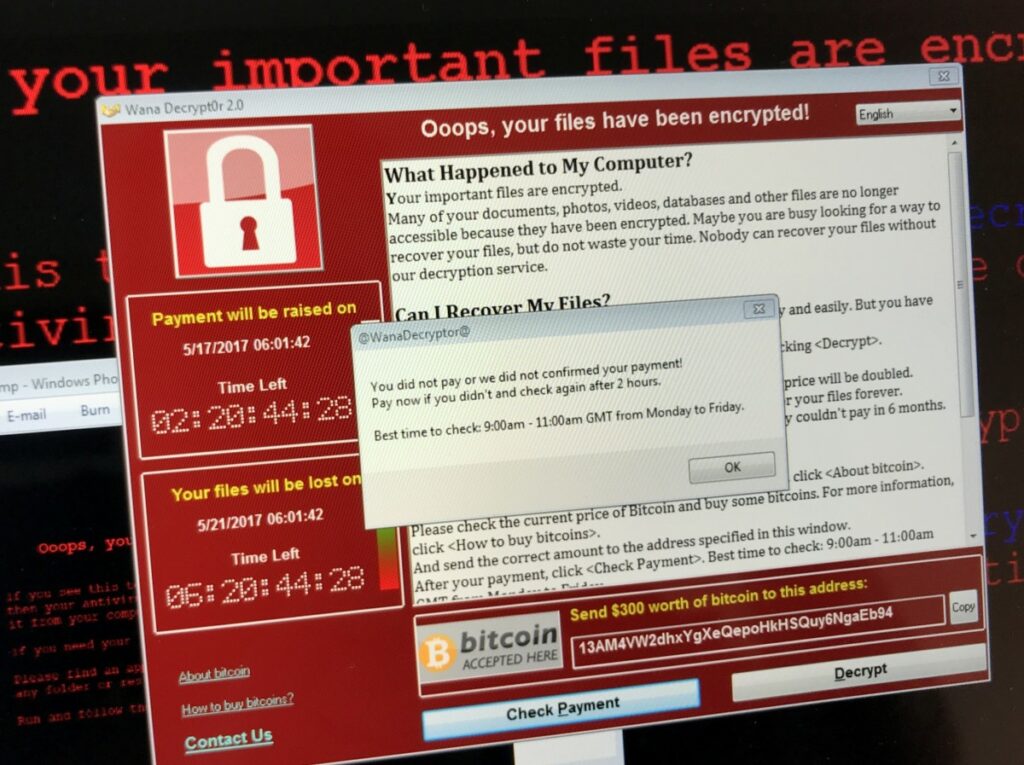
In recent years we’ve seen a spate of headlines relating to ransomware. The 2017 WannaCry attack, for example, affected over 200,000 devices in more than 150 countries. In the UK alone it’s thought to have cost £92 million.
This isn’t a problem that’s going away. According to SonicWall there were 304.7 million ransomware attacks in the first half of 2021.
Three quarters of businesses attacked by ransomware experience at least two days without access to their files.
Ransomware is a major cyberthreat and your company should be taking action now to prevent it.
What is ransomware?
Ransomware is an cyberattack whereby criminals secrete code on your computer system which encrypts your data and results in a ransom demand to decrypt it.
How do ransomware attacks happen?
Commonly they start with a phishing email. This is an email made to look like it comes from a genuine organisation, such as a store or government, or even a friend. The email encourages you to click on a link or open a file. This then downloads the ransomware code onto your computer.

Other methods of infection include employees connecting infected personal devices to the network, plugging in a spiked USB device or downloading a file from a website.
Once the code is embedded in your computer, it sends a message back to the attackers’ “command and control” server with an encryption key.
Once the encryption key has been transmitted, the ransomware will then proceed to encrypt all your data. This will happen on your PC and anywhere else it can get to – which could well be your entire company network. It will create an encrypted version of every file and then delete the originals. You’ll then see a ransom note appear on your screen. The ransom demand is often in bitcoins, as this virtually untraceable currency makes it much easier for the criminals to get away with it.
This phishing email, used in the CryptoLocker ransomware attacks, claims that the recipient has been fined for negligent driving. Naturally, the reader’s first instinct is to click on the link to see details of the infringement, but unfortunately that click downloads the ransomware onto their device.
Gangs may also steal your files before encrypting them. This then becomes a second threat to your organisation – that of the potential data breach should the files be published.
How to stop ransomware
Preventing infection
Firstly, make sure that your antivirus and antispam software is up to date. Check its scans include compressed or archived file types. This will prevent the majority of phishing emails getting through, and significantly reduce the threat.
In the case of Microsoft 365, if you have a Business Premium licence, all email attachments are assessed for suspicious activity and not delivered if any is detected. It also has a Safe Links feature which checks that hyperlinks aren’t sending you anywhere dodgy. If you have Business Basic or Business Standard then these are available as add-ons.
Your firewall, such as the Windows Defender Firewall, is another line of defence and should always be turned on and correctly configured.
Ensure that pop-ups are blocked by default in your internet browsers as these are another common entry point for an attack.
Establishing a list of allowed applications, and preventing the download of any not on this list, will reduce the risk of infected software being downloaded. Equally, keep people’s system access to the minimum needed, so if an account is compromised it will only provide limited access to your system.
However good your defences, some attacks will always get through. So it’s essential that all your staff receive regular cyber awareness training. This will teach them how to spot the threats and what to do about them. It will also give them advice on securing their accounts, such as using strong passwords.
Preventing encryption
Devices protected with Microsoft Defender Antivirus, or similar anti-malware systems, should give your common folders, such as your Desktop or Documents, protection against unauthorised access. This may prevent them being targeted by ransomware.
All of these defensive applications, and Windows itself, should be kept up to date. Don’t ignore a Windows update request – it may include a security patch which will prevent tomorrow’s ransomware attack.
If these defences don’t work, then there’s a chance that your server security tools will detect the message being sent back to the attackers’ command and control server and block it, however this can’t be relied upon.
Preventing spread
You should always monitor your network for suspicious activity. If the attack gets as far as encrypting your data, you will see a spike in your storage activity, which is your last chance to at least reduce the data loss.
Systems such as Microsoft Defender Endpoint provide automatic monitoring of your systems and can remedy any threats they spot.
If you catch the attack before it spreads, immediately disable your internet connection. Most ransomware attacks need the connection to their command and control server to implement the encryption. Don’t reconnect to the internet again until an expert has identified and removed the ransomware program.
However, if the encryption has completed, you only have two options: pay up or restore from backup.
Paying the ransom
We say two options, but paying up really isn’t one you should consider. You have no guarantee that you’ll receive the encryption key and ever recover your files. And, if they’ve stolen your data, you can hardly take their word for it that they’ve destroyed it once the ransom has been paid.
Plus, frankly, paying up means you’ll be funding a criminal organisation and perpetuating the problem.
Restoring from backup
Instead, you will have to restore your files from backup. Assuming you back up frequently, your data loss will be minimised to just the file changes since your last back up.
Restoring the files will be a much quicker solution than decryption. If you use the Microsoft OneDrive, for example, all your files are automatically backed up and version controlled, so you can simply restore to a date and time earlier than the attack.
But the best solution, of course, is to prevent an attack in the first place.
How Heliocentrix can help
We provide security advice and installations, ensuring that your IT systems are protected against ransomware and other cyberattacks by layers of defence.
This includes training your people to ensure that they don’t in advertently let an attack slip through the net.
Call us on 01732 600 170 or email [email protected] to find out more.
