Do you ever experience the fear of opening your email? Of discovering how many new messages have been added to your already-hideously-large inbox?

These feelings are very real and very common. And, while we might joke about them, they can have significant impacts on employee efficiency and wellbeing.
For organisations this can create a hidden drain on productivity.
A study by Gloria Mark at the University of California indicated that employees who spent more time on email each day felt they had been less productive overall. In addition, increased time spent checking email was also associated with higher levels of stress.
In this article we look at 21 ways to better manage your emails, to increase productivity and reduce the stresses of email overload. And we discuss how Microsoft 365 can support you in achieving inbox nirvana.
Get the right infrastructure
Life is too complicated not to be orderly.
Martha Stewart
1. Use the right software for the right task
Email software, such as Microsoft Outlook, is excellent for managing emails. But that doesn’t mean that it’s a great workflow management system or that it can be your CRM application.
Trying to manage complex activities involving multiple people, or tracking and sharing important customer information, is not a job for your email system. You won’t be able to carry out these activities effectively and will put unnecessary strain on your inbox.
Instead, invest in systems which were developed to do the tasks you need, and which work alongside your email client. That way you can enjoy smooth and efficient integration between your emails and other activities without clogging up your inbox.
2. Banish spam
Billions of spam emails are sent around the world every day (source: Statista), so ensuring that as few as possible hit your inbox is the first step in managing your email volumes.
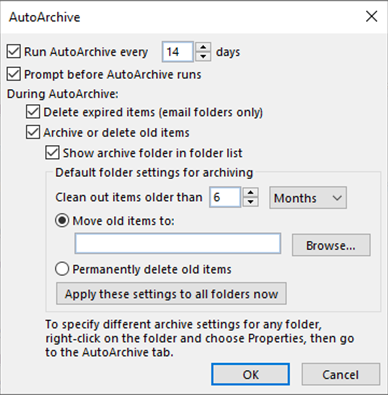
With a robust anti-spam technology, such as that offered by Microsoft Exchange and Microsoft 365 Defender, you should receive very few spam emails. The vast majority will be stopped before they reach your inbox. Of the few that do get through, most of those will be automatically sent to your ‘Junk Email’ folder.
If any do make their way into your inbox, make sure you right click and select Junk then Block Sender before you delete the email, to ensure that no more arrive.
It’s also useful to occasionally check your ‘Junk Email’ folder to make sure no legitimate emails are in there. You can let Outlook know that they aren’t junk by right clicking and selecting Junk then Not Junk.
Note that you can ‘dial up’ or ‘dial down’ the strength of your spam filter. If too many emails are going into junk or quarantine you might want to dial it down a bit. However, if too many are landing in your inbox, then dialling it up should help.
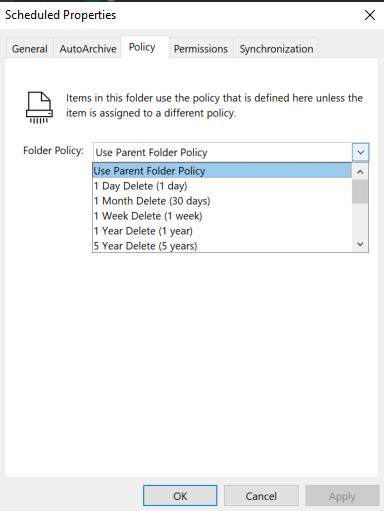
3. Using folders wisely
Setting up an efficient email folder system will be enormously helpful in sorting through your current inbox and managing future email arrivals.
There are a few different ways you can consider organising your email folders.
Minimalist and efficient
An approach which requires fewer folders is generally the best solution. Having too many folders can cause Outlook to operate more slowly, because you’re asking it to synchronise more folders with the cloud (read more about how to speed up Outlook). It will also take you longer to organise your emails if you have too many folders to sort them into.
The excellent sort and search functions in Outlook means that, even if you have only a few folders, it’s still easy to find emails from a particular person or on a particular topic.
You might, for example, have these folders:
- Need to reply
- Need to action
- Need to read
- For reference
- Archive
Or perhaps organise your emails into days of the week according to when you’re going to deal with them:
- Monday
- Tuesday
- Wednesday
- Thursday
- Weekend reading
Or simplify it even further by following the Marie Kondo method for managing paperwork, which involves discarding almost everything and sorting everything that remains into two categories:
- To be saved
- To be dealt with
The two-folder method is the one we advocate.
A bit less minimalist
If you can’t bear the thought of only having a few folders, then at least make sure that the ones you have are for essential reasons. Perhaps one for each major project or one for each major client (minor clients can be bunched together in one folder as you probably don’t get many emails from them).
In addition, you might find it useful to have a general ‘reference’ or ‘things to read’ folder for items of general interest or reference.
4. Focus on what is important
Most major email services will automatically sort your inbox for you, to help you prioritise the most important emails. In the case of Outlook, it sorts it into your ‘Focused’ and ‘Other’ inboxes.
Outlook learns what emails are important to you by monitoring how you deal with each email that arrives in your inbox. After a few weeks of using it, Outlook learns which emails are your priority (which will be sorted into ‘Focused’) and which are not (‘Other’).
This gives you an immediate aid to managing your inbox.
And, if Outlook gets it wrong, you can help it to learn by right-clicking on the wrongly categorised email and selecting to Move to Other or Move to Focused as appropriate.
5. Unsubscribe from email newsletters
When each email newsletter lands in your inbox, think carefully about whether you really want to receive it. Will you actually read it? Is it useful or interesting to you?
If the answer to any of these is “no” then unsubscribe from it. Don’t just mark it as junk or delete it – actually unsubscribe so it never clogs up your inbox again.
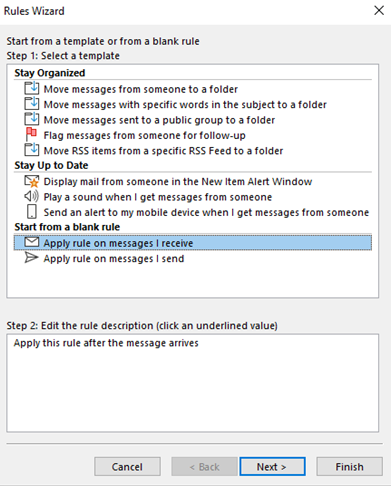
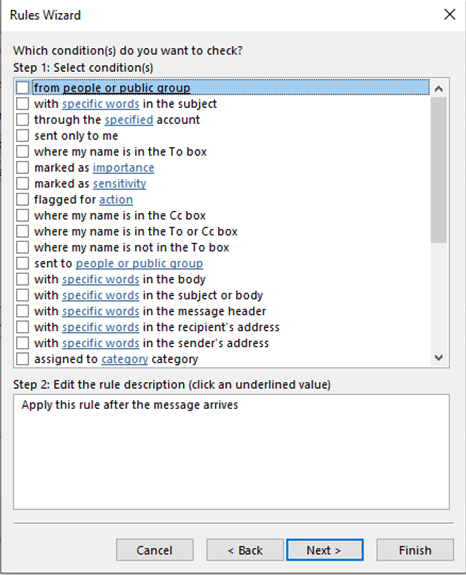
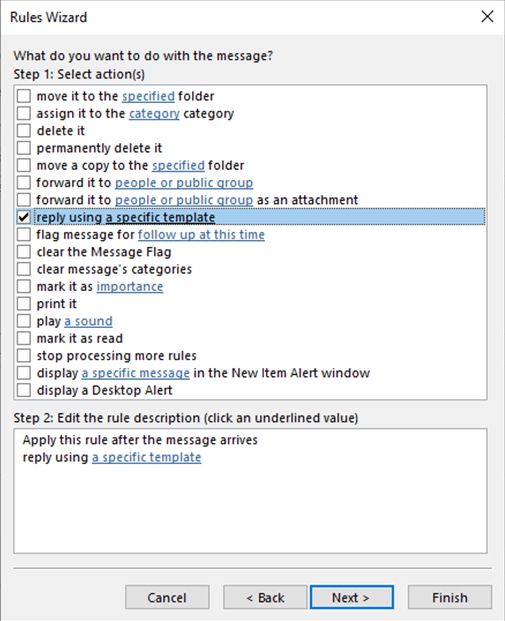
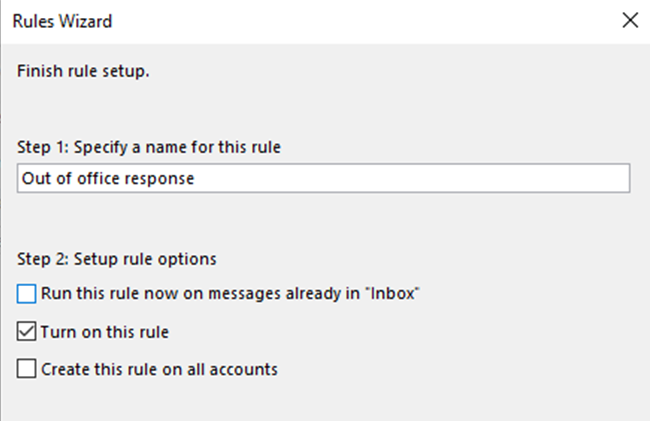
6. Rule your inbox
Rules are another hugely time-saving way of clearing your inbox.
In Outlook you can set up rules which take actions for specific types of email, based on criteria such as who they are from and the subject line.
Outlook can then take specified actions for each type of email. For example, if you receive regular newsletters or company updates it can automatically move them to a ‘Things to read’ folder. If you need to prioritise emails from a particular person it can flag these emails or even send an alert to your phone when they arrive.
Get down to zero (or near enough)
The best way out is always through.
Robert Frost
Once you’ve organised your email structure and rules, the next step is to deal with your current inbox. It’s big… it’s scary… but it has to be done.
7. Plan in time for a bit clear out
It’s easy to put off sorting out an overloaded inbox which you’ve been ignoring for weeks or even months. The task can feel overwhelming and impossible. However, the relief you’ll feel when it’s done will make it well worth the effort.
The easiest way to make sure you get it done is to plan it into your diary as you would for any other major piece of work. Assume it’s going to take a whole day – if you get it done sooner that’s a bonus.
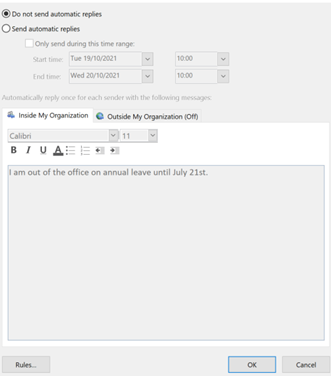
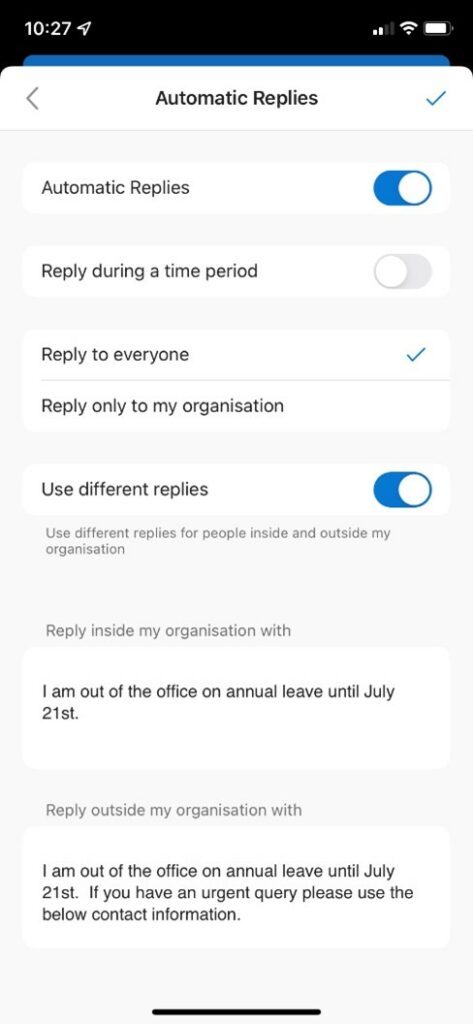
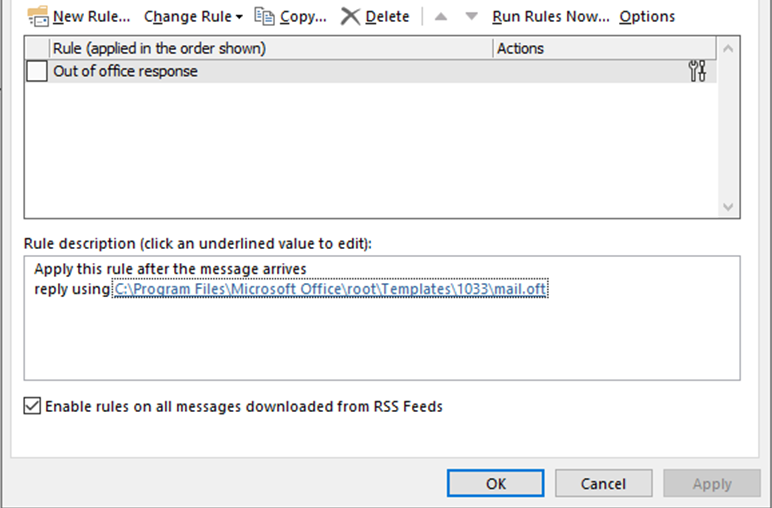
Tell people you won’t be available and put an out of office response onto your email and phone for the day.
8. Get away from your desk?
One of the major benefits of Microsoft 365 is the ability to work anywhere anytime, and you can use this to your advantage to get your inbox cleared.
Working at your desk in the office might not be the best idea, as it’s too easy to be distracted by colleagues and, let’s face it, more interesting things than clearing out your emails.
Working from home is one solution. But you might find that a trip to your local café makes the job more enjoyable.
The important thing is that you are working in an environment with few distractions.
9. Stop the flow
When you start working on your inbox it’s a good idea to turn your email offline, so new emails don’t start popping up while you’re working. In Outlook you do this by going to Send / Receive in the navigation menu and selecting Work Offline.
What to do with all those emails
It's fine to decide not to decide about something. You just need a decide-not-to-decide system to get it off your mind.
David Allen
Now you have your email structure in place and the time to deal with your inbox. So next you need to think about how to process each individual email.
10. The 2 minute rule
In David Allen’s book Getting Things Done he has a simple system for assessing each email. First of all, do you need to take an action as a result of this email? If not, delete it or store it in an appropriate folder.
If it is actionable, will it take 2 minutes or less to complete? If the answer is yes, do it.
If it will take longer than 2 minutes, then decide if it can be delegated. If it can, delegate it. Delete the email or file it in an appropriate folder.
If it will take longer than 2 minutes, but can’t be delegated, then you defer it. This means moving the email to an appropriate folder and adding the action to your to do list or, if it has to be done on a particular date, to your calendar.
Through this process, every email will either be dealt with quickly or you can file it away safe in the knowledge that the action required is listed somewhere. See points 12 and 13 below for ideas on how to use Outlook to manage actions through tasks and calendar.
11. Flagging emails
When you move emails into folders it can be useful to add a flag onto any which need to be dealt with, so they become easy to identify.
This means that you can then either sort the folder by Flagged Mail to see all the ones you’ve marked. Or you can add a Flag Status into your options when you search in Outlook, so the search only returns flagged emails. This is a really useful method, though it’s important to be disciplined about removing the flags (or deleting the emails) once the action is completed.
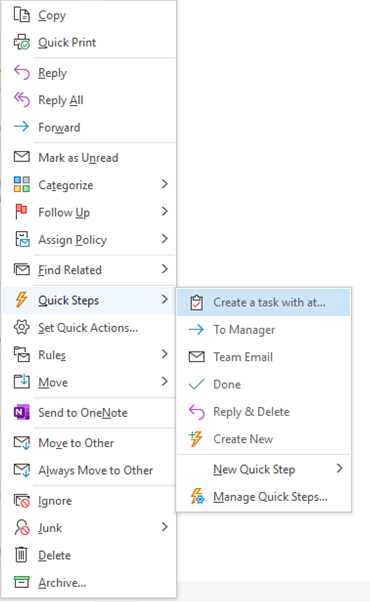
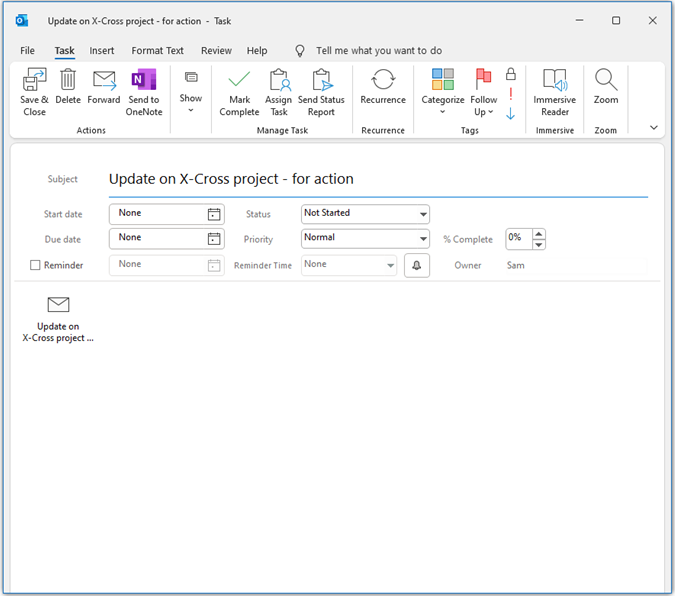
In Outlook you can also flag an email so it automatically adds to your task list/To Do list. To create a task from the email, right click on the flag icon and select Add reminder.
12. Managing actions through tasks
A to do list is an excellent way of recording actions from emails. The task function in Microsoft Outlook makes it straightforward to link emails and tasks. Creating tasks might sound like you’re just duplicating the email, but you’ll find that a single task probably relates to many different emails.
Outlook tasks have plenty of functions which make it easy to organise your email actions:
- Attach function which allows you to attach emails or other files to the task.
- Colour-coded categorisation to help you sort your tasks.
- Automated reminders.
- Recurrence function for repeating tasks.
- Ability to assign the task to someone else.
Once all your actions are safely in your to do list, then you can simply review your tasks on a daily or weekly basis, depending on how often you like to plan your work.
Outlook tasks can also be integrated with other Microsoft applications, such as OneNote and Sharepoint.
13. Managing emails through a calendar
In the Getting Things Done model David Allen suggests that the only tasks which should go into your calendar are those which have to be done on a particular date. That way, when you open your calendar in the morning, it doesn’t look too overwhelming.
However, if you prefer, you could use your calendar as the single place to manage all your actions from your emails.
In Outlook, creating a calendar entry from an email is quick and easy. You simply right click on the email and select Move then Calendar. Outlook will automatically set up a new calendar entry, using the subject of the email as the title and with the email itself attached.
As with Outlook tasks, the calendar also includes functionality such as colour-coding, reminders and repeated events.
Learn new habits
Productivity is never an accident. It is always the result of a commitment to excellence, intelligent planning, and focused effort.
Paul J. Meyer
Once you’ve completed the job of clearing your inbox (well done!) you need to keep it that way.
14. Decide how often to check your emails
Research for University College London by Adam Bradley, Duncan Brumby and Anna Cox in their paper How to Manage Your Inbox: Is a Once a Day Strategy Best sought to discover whether checking your emails just once a day can reduce the pressures of email overload.
They found that, firstly, most participants in the study struggled to only check their email once a day, although they did manage to check it less than normal (down from 8 times a day on average to 3.6 times). They found that checking emails less frequently gave participants a significant time saving in terms of overall time spent on email management.
So, scheduling in specific time in your day to check your emails, and not checking them at other times, could be a useful way of managing your inbox more productively. Remember, people really don’t expect you to reply to every email within five minutes – and if anything is that urgent they can always call you.
You can also consider other opportunities in your day when you could take just a few minutes to clear out some emails. For example if you’re in a waiting room, queue or hanging around to pick up your children, use the time to clear out a few emails on your phone. Other tips to get more from your day with your phone.
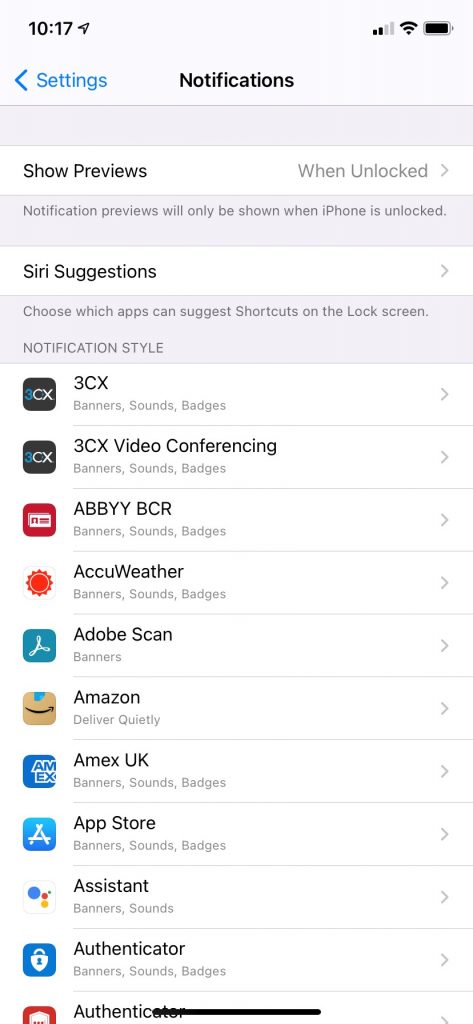
15. Email notifications
Once you’ve made a decision about when you are (and are not) going to check your emails, turn off your email notifications.
Email notifications encourage you to check your emails more often than you want to. These interruptions into your working day also mean you waste additional time ‘reorientating’ yourself back into the task you were interrupted from. Gloria Mark’s research for the University of California showed that participants who only checked their email when they wanted to felt they had been more productive, compared to other participants who checked their emails each time a notification arrived.
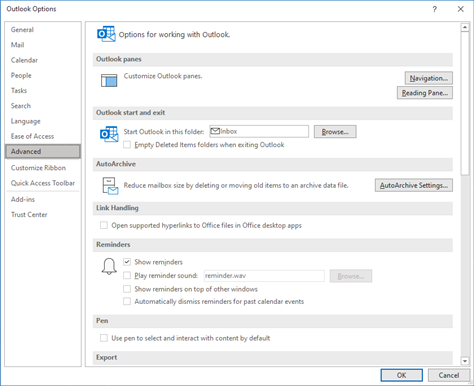
To turn off your notifications in Outlook go to File, Options and then Mail. You’ll see a section titled Message arrival. You can untick all of these to ensure that you aren’t interrupted every time an email arrives.
16. Weekly slot to get down to zero
While you might need to check your emails a few times each day, you don’t necessarily need to feel pressured to get your inbox to zero every day (although this does suit many people).
However, it’s good practice to get into the routine of reducing your inbox to zero at least once a week.
It helps to have a regular, weekly slot for clearing your inbox. Book a regular event out in your calendar each week to clear your emails. That way you won’t get stressed if your inbox starts to build up a bit, because you know you’ll get it all dealt with in your regular timeslot.
If your regular email clearing time is in the evening or at weekends (not ideal, but it might be the best time for some people) you may find the Delay Delivery function in Outlook’s Options menu useful. This can schedule your email to send at a date and time you specify. So, if you’re clearing your emails on a Saturday morning, but don’t want to trouble your colleagues with emails on the weekend, you can schedule them to send on Monday morning instead.
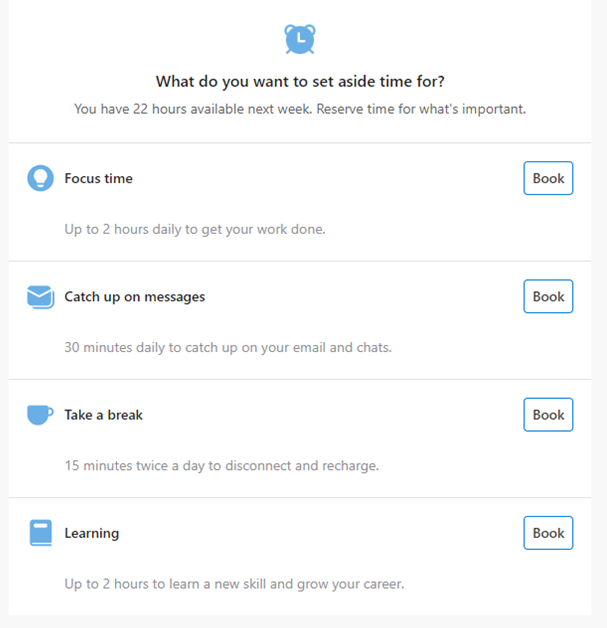
On a side note, Microsoft provides you with a range of personal insights into your working activity. These can help you to set aside specific periods each day to focus on tasks rather than emails. It can also help you to track how often you’re working outside your normal hours to ensure you’re not burning the candle at both ends: https://myanalytics.microsoft.com/.
17. Template responses
In Microsoft Outlook there’s a handy ‘Quick Parts’ function, which can be very helpful if you often send emails with the same content. It enables you to save chunks of text and then insert them into new emails.
To save a ‘Quick Part’, start an email and type in the text you want to save. Highlight the text, go to Quick Parts in the menu and save the text. When you type a new email, simply go back to the Quick Parts menu and your saved text will be there, ready to be inserted. Alternatively, you could install the Outlook plugin ‘My template’ which provides similar functionality.
18. Learn shortcut keys
When going through your emails there are a number of shortcuts you can use in Outlook to speed up the process, including:
- Esc to close an email.
- Alt+S to send.
- Backspace (not delete) to send it to your archive folder.
- Delete to delete.
- Ctrl+Shift+K to start a new task.
- Ctrl+2 to switch to the calendar.
View the full set of shortcuts.
Let people know what you need
Bad human communication leaves us less room to grow.
Rowan Williams
Everyone has different preferences for dealing with emails and we don’t often think about how our methods impact others.
Letting your colleagues know how you prefer to receive emails could make your life a lot easier, particularly if you’re working with people who use emails in a very different way to you. Of course, the key to success is to reciprocate and email them according to their preferences.
Here are some practices you might ask them to adopt:
19. No thank you
You might request that colleagues don’t send non-essential ‘thank you’ emails.
Perhaps explain that you’re very happy to receive thanks if you’d done something stupendously amazing, but if you’ve just emailed them the document they asked for, then thanks is not required.
20. Ask for clear subjects
Having clear subjects for emails you receive makes it much easier for you to skim through them and identify what needs to happen with each one.
21. All in one or one for each
Some people prefer to have one email for each subject. Others would rather only receive one email a day from each colleague covering multiple topics.
If you have a particular preference, then share this with your team too.
Discover more ways to enhance your productivity
Heliocentrix is a strategic IT consultancy based in the south east of England. We work with businesses to define and implement the optimal IT strategy to increase their employees’ productivity, wellbeing and enjoyment.
Find out how we could help your organisation.